Steradian Data
Optima Solution
Empowering Everyone


Our Target
Steradian Data Optima Cyber Security is one of the leading cybersecurity companies in the asean region. We deliver end-to-end cybersecurity services and solutions from bacis continuity SDLC Devops to (Software Development Life Cycle) to Dev”Sec”Ops, including Security Solutions Integration, and Managed Security Services. Steradian provides continuous IT infrastructure protection against multiplying cybersecurity threats and ensures compliance with increasingly demanding data protection and critical infrastructure regulations.

Our expertise has been built over a decade of delivering thousands of high-quality cybersecurity projects, providing cutting-edge solutions in collaboration with world-class technology partners across financial, telecommunications, energy, transportation, manufacturing, and other critical industry sectors. We also have extensive experience in helping our customers with fraud prevention, Operational Technology (OT), and Industrial IoT (IIoT) security.
Red and blue teams are cybersecurity teams that work together to strengthen an organization's security defenses: · Red team, Simulates cyberattacks to find vulnerabilities in a system. Red team members use the same skills and tools as malicious hackers, but their goal is to improve network security.
Blue team, Defends the system from cyberattacks by monitoring for threats, detecting breaches, and applying security measures. The red and blue teams work together to create a feedback loop where each exercise strengthens the organization's overall security posture. The terms "red team" and "blue team" are originally from the military, where red teams think like the enemy and attack, and blue teams try to defend.
Identity and Access Management Services (IAM) Tools are middleware solutions used to manage digital identities and user access rights within a system, application, or IT infrastructure. The main purpose of IAM tools is to ensure that only authorized users can access resources in accordance with the roles and security policies of the organization. Identity Management (IdM) and Access Management (AM) are the two main components in an Identity and Access Management (IAM) system. Although the two are often referred to together, they have different focuses and functions.
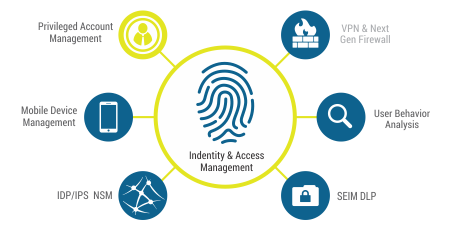
Privileged Access Management (PAM) is a security solution designed to protect, manage and control access to privileged accounts within an organization's IT infrastructure. PAM helps prevent security threats such as credential theft, unauthorized access, and misuse of privileged accounts. This solution can perform account and password management on servers.